Project description
Main focus and common objectives
The use of mobile devices (smartphones, mobile phones, PDAs) expands further and they become more frequently integrated in corporate networks. Especially security relevant business processes are operated with mobile devices (M-Business, M-Commerce) and these devices manage more often sensitive data, too. The introduction of new platforms for smartphones, like iPhone or Android Mobile Phone G1, enlarges the range of functions for mobile phones, which are now comparable to PCs. Both platforms provide the opportunity to download plenty of new applications. This increased complexity of end devices, which is at the same time linked to a higher mobility and an increased demand of greater connectivity enlarges the risk of compromising malware and targeted attack, without knowledge of the user. This can affect the availability and safety of IT-infrastructures, because security policies of various companies can be circumvented in this way. More than ever the combination of telephone and PC functionalities can cause safety risks that aren’t yet adequately studied and understood. This especially applies to software of mobile devices that leads to security gaps like buffer overflows. Lately, a series of security problems has just became known in new platforms like attacks on iPhone, symbian end devices and recently even on Andriod Mobile Phone G1.
Considering for example the scenario of a company guest, connecting to the company network with his mobile phone, shows that safety requirement issues are related to mobile devices. At first a secured access to the IT-infrastructure through a suitable authentication is required. Furthermore the device has to be in a trustworthy condition to ensure that no malware is transferred to the network. To classify a device as trustworthy, the newest patches and a personal firewall should be installed. A security policy of a company can also ensure that only specific applications can be installed. To enforce the corresponding security rules for devices, suitable safety mechanisms have to be implemented.
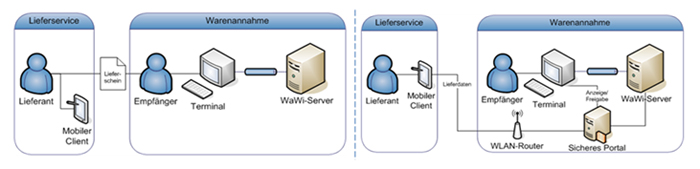
In addition, supply chains and general organization scenarios are also interesting. In this context, e.g., a modern federated identity management system (IdM) can be named, in which digital identities are represented by mobile devices and where supply chain partners will automatically be announced. These “portable identity” have to be trustworthy to prevent an unauthorized user access to safety-critical applications such as ERP systems. On the other hand, a mobile device is exposed in organizational scenarios to external attacks.
Due to the new and growing requirements that are provided for the trustworthiness of mobile devices, a platform is being developed in this project to secure these devices. In particular this safety platform will provide mechanisms for trustworthy equipment authentication. With the "guest mobile access to company networks" scenario especially with the focus on VPN solutions (virtual private network) the security benefit will be demonstrated. The safety solution for mobile devices developed in VOGUE will not only be limited to the application scenario just mentioned, but could also be used to secure mobile applications in general.
Scientific and technical objectives
The mechanisms and specifications of the Trusted Computing Group (TCG) are intended to provide the basis for the security platform. This means above all that Trusted Network Connect (TNC) can be used allowing mobile end-devices (laptops in particular) to access the infrastructures of organisations in a trustworthy manner. Until now transferring this approach to mobile phones has not been the subject of R&D projects. It is a favourable point in time to realise such a project, because Android, an open platform, now permits application development on mobile devices, thus also enabling the realisation of security mechanisms for TNC and the integration of Trusted Computing. This aspect will be one of the core themes of the proposed VOGUE R&D project. Such a TPM for mobile systems is currently specified by the respective firms and will soon be introduced into the market. An emulator is being developed to allow the development of products for this emerging security technology.
In order to achieve independence from large manufacturers open source solutions are in general supposed to provide the basis. This will allow small and medium sized businesses to offer services such as protected VPN applications to mobile employees independently from large providers. Such services will be integrable into existing solutions. Where possible the results will be made available to the open source community again. The targeted project's security platform offers small and medium sized businesses an entry into the provider-independent development of secure solutions for the continuously growing mobile applications' market.
VOGUE is addressing exactly these questions within the context of mobile phones and will show on a demonstrator that Trusted Computing can augment security and trustability levels in this area as well. Also, industry is showing an interest in secure solutions for mobile end-devices based on Trusted Computing.
The results of the VOGUE project are listed below:
- Tapped/tapping into the emerging market of TPM based solutions within the mobile area for the industry in Germany
- Developing a basis for trials of TPM-based solutions while using an emulator that enables small and medium sized businesses to enter into this new business field
- Facilitate security relevant and mobile business processes by establishing a trustworthy platform for mobile end-devices. This will, for example, prevent possible attacks and/or reduce the damage that may occur through attacks
- Demonstration on the basis of a distributed platform for mobile end-devices

